Projects in Cyber Security
Patrol: Identifying Zero-day Attack Paths in Enterprise Networks
Knowing whether an attack has indeed happened is especially difficult to achieve when the attack leverages unknown security holes. To reach the final attack target, attackers often have to go through an attack path via several stepping-stones. If an attack path contains one or more zero-day exploits, it is regarded as a zero-day attack path. Due to leveraging unknown vulnerabilities, zero-day attack paths are often obscure and hard to detect.
Although related work can be found in attack graph, intrusion detection, and alert correlation, no existing techniques are readily available to well address the zero-day attack path problem. By combining vulnerabilities existing in a network, attack graphs are able to generate attack paths that show exploit sequences. However, the generated attack paths only contain exploits towards known vulnerabilities. Alert correlation can correlate isolated alerts to form possible attack paths, but suffers from high false rates. Anomaly intrusion detection is capable of detecting novel exploits, but also has difficulty coping with false positives.
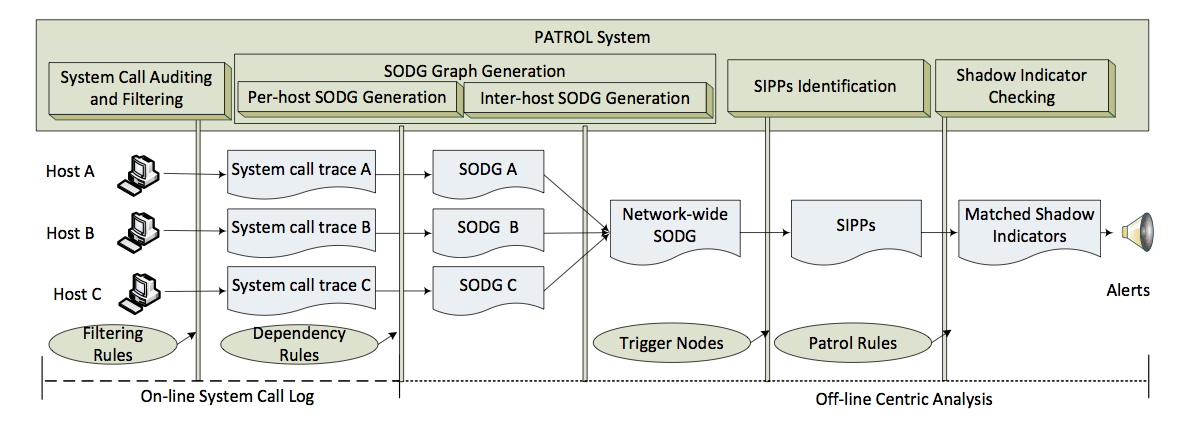
We present a system called Patrol, which takes a quite different strategy for zero-day attack path identification. Instead of collecting vulnerabilities or alerts and then correlating them into paths, we first build an operating system level superset graph (System Object Dependency Graph) that captures both normal system activities and malicious attack activities, and then identify suspicious intrusion propagation paths through tracking and shadow indicators.
CloudBN: Inferring Stealthy Bridges between Enterprise Networks in Clouds
As enterprise networks constantly adapting themselves to new technologies, new security risks also emerge. One example is the “stealthy bridge” problem posed by the migration from traditional infrastructure to cloud environment. Except for some public services, enterprise networks residing in public cloud are expected to be absolutely isolated from each other. However, some “stealthy bridges” may be created to break such isolation due to public cloud’s features of virtual machine image sharing and virtual machine co-residency. Attacks on cloud can compromise several enterprise networks residing on the same cloud.
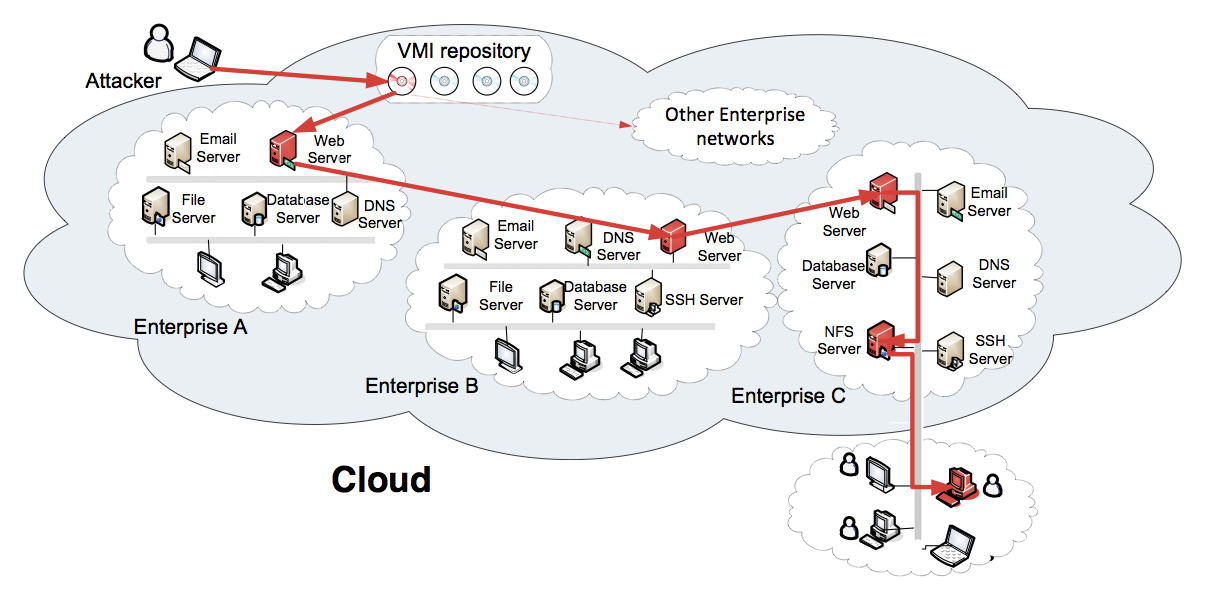
We propose a probabilistic approach to infer the existence of stealthy bridges. This approach is supported by a fundamental underlying insight: given a multi-step attack inside the cloud, although stealthy bridges per se are hard to detect, the intrusion steps before and after the stealthy bridges can often be noticed by security sensors or human administrators. Constructing cloud-level attack graphs and cross-layer Bayesian networks are two most important steps to capture potential attacks enabled by stealthy bridges and quantitatively compute the probabilities of interesting events.
MTA-BN: Towards Mission Impact Assessment
An effective attack can lead to great loss in the confidentiality, integrity, or availability to missions, and even cause some to an abort in extreme cases. When an attack happens, one major concern to security analysts is how the attack could possibly impact related missions. System level dependency graphs and Bayesian networks have provided a solid foundation for solving this problem. If mapping high-level missions to low-level system objects is viable, impact of system level attack activities towards high-level missions can be reflected through information flow tracking and uncertainty analysis.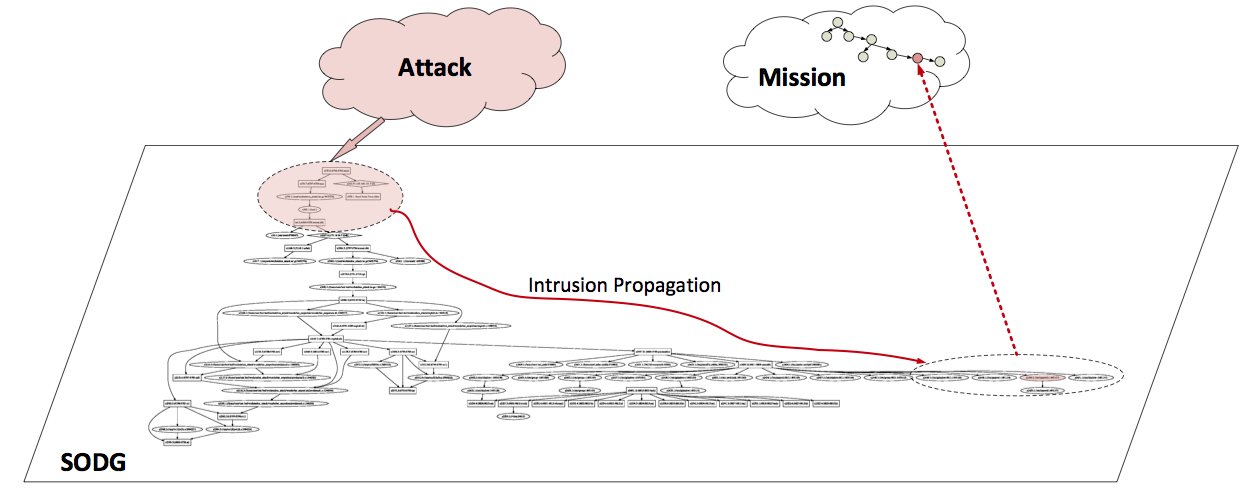
SKRM: Achieving Big-Picture Cyber Situation Awareness
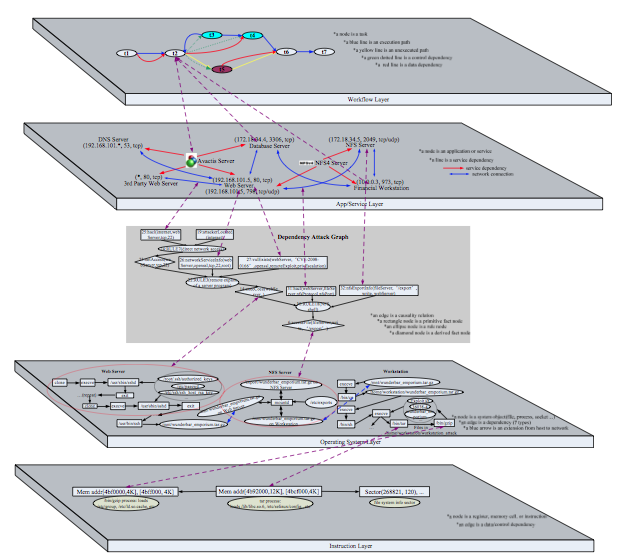
Situation awareness is the prerequisite for cyber security intelligence. Before reacting to attacks, network defenders should clearly know what is going on in the network. This is basically what we call cyber situation awareness (cyber SA).
In the past decades, a rich set of security solutions have been developed to yield helpful situation knowledge, such as vulnerability analysis, intrusion detection, damage and impact assessment, and system recovery, etc.However, these solutions are usually restricted and isolated by their corresponding abstraction levels, such as workflow healing at business level, attack graph analysis at network level, system object dependency tracking at operating system level, etc. These solutions cannot “talk” directly to each other to reach an agreement. We formally recognize this problem as “stovepipe” problem. Security analysts are easily immerged in the sea of data and can hardly put the evidence into a “story” that tells what happened to the network. Hence, we proposed an SKRM (Situation Knowledge Reference Model) model to integrate data, information, algorithms/tools, and human knowledge into a whole stack. SKRM serves as an umbrella model that enables effective analysis of complex cyber-security problems.